This task i performed recently and i was fortunate that AWS started supporting IKEv2 , prior to this news we could perform subjected task by spinning 2016 server and enabking RDS but now we can use the cloud for this Site-to-Site VPN.
This task would be exactly same as any other Site-to-Site connectivity. Steps involved :-
Azure : AWS :
Create Virtual Network Create VPC
Create Gateway Subnet Create Customer Gateway
Create Virtual Network gateway Create Virtual Private Gateway
Create Local network Gateway Create VPN Connection Statically
Update gateway with Pre-shared Download configuration file for details
Update LNG with IP (config file AWS) Attach Virtual private gateway to VPC
Create Connection Update route tables for VPN
Below are the relevant snippet : -
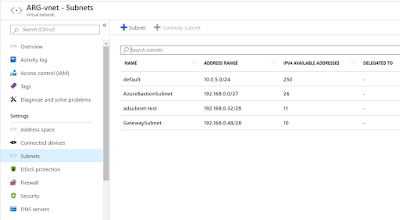
This is the Vnet created in the Azure with different range of subnets including Gateway subnet.
This is Virtual Network gateway we created with static route and vpngwy1 sku -
Now once we have created vnet and gateway on Azure , simultaneously we created VPC , subnets and customer gateway(static) on AWS. IF you compare with Azure customer gateway is like Local network gateway where you add the Public IP of Virtual network gateway on Azure -
This task would be exactly same as any other Site-to-Site connectivity. Steps involved :-
Azure : AWS :
Create Virtual Network Create VPC
Create Gateway Subnet Create Customer Gateway
Create Virtual Network gateway Create Virtual Private Gateway
Create Local network Gateway Create VPN Connection Statically
Update gateway with Pre-shared Download configuration file for details
Update LNG with IP (config file AWS) Attach Virtual private gateway to VPC
Create Connection Update route tables for VPN
Below are the relevant snippet : -
This is the Vnet created in the Azure with different range of subnets including Gateway subnet.
This is Virtual Network gateway we created with static route and vpngwy1 sku -
Now next step is creation of Virtual Private gateway on AWS , it is like Virtual Network Gateway on Azure but it will not show you Public IP and you need to attach this to VPC manually not like Azure
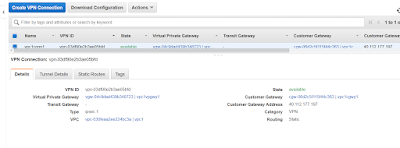
Now we would also update VPN connection on AWS where we would provide the details of Vnet address spaces & static routing and once its created you can download the configuration for LNG.on azure.
Now its time for Local network creation on Azure which would contain the address space of AWS VPC and Public IP of aws gateway. Azure details you can find once you will download the details from AWS VPN Connection pane at the top it says Download configuration inside that configuration you will find the Public IP and pre-shared key for IPsec tunnel # 1.
Now create the connection as all the relevant information is already completed -
you will see in few minutes it would show connected and you would be able to ping AWS machine if route tables are updated properly.








It says that IPSec is UP but tunnel is DOWN on AWS side. Can't ping even with routes + SQ. Any thoughts? Thank you for writing this article :)
ReplyDeleteSure check the VPN connection settings on AWS side and LNG on Azure side , may be something is missing second check the route table if unable to ping - try this or if already resolved please share the findings.
DeleteResolved, I was using Terraform to bring up the tunnel on AWS side and I forgot to specify to use something called vpn_connection_static_routes_only = true. I mistakenly thought that I could just add the static route in the route table. It's working now. Anyone who follows this guide should work for them since I happened to be using Terraform instead of inputting directly in AWS console. Thanks for the reply :)
DeleteThanks for sharing Sam
Deletehealth supplements germany
ReplyDeletehealth supplements guernsey
health supplements guelph
health supplements gst
health supplements geelong
health supplements glasgow
health supplements gold coast
health supplements galway
health supplement hs code
health supplement hsa