Azure AD Identity protection helps
to Automated response to "risk and vulnerabilities" & you need AD P2 license.
Well as name suggests it helps to
make your environment more secure by increasing the security of user identities
by –
·
Detecting potential vulnerabilities affecting
user identities. (user has history to login from certain place now if he logins
in from other places or VPN instead of office )
·
Configuring conditional access policies to
automatically respond to suspicious actions. ( this a wonderful feature that
you can enable with conditions like asking for MFA if location is unknown or
not in office)
·
Investigating suspicious incidents and resolving
them automatically. (no constant auditing and overcome admin work and harden
user identities)
What AD Identity Protection is?
Stolen user identities are the
number one cause of security breaches. Attackers leverage phishing attacks and
malware to gain access to systems. (Get emails from known places like MS and
they ask your information and it could easily leak from allowing access to your
phone when you install app. )
Admins must protect all identities
, no matter the privilege level or low level and ensure that compromised identity do not
gain access.
This typically involves full-time
awareness and monitoring of all user identities. The administrative effort is
huge and most of the time its completely reactive in nature.
Azure AD Identity protection
removes much of this effort by providing comprehensive solution that is :-
·
Proactively prevents compromised identities from
accessing resources.
·
Provides recommendations to improve security by
analyzing vulnerabilities, such as user and sign-in risk levels and risk events,
as well as environmental factors
·
Notify admin of risk events.
·
Allows admin to create policies to automatically
mitigate risk events.
Azure AD Identity protection Components:
-
Lets understand these components one by one -
1) Notifications
2) Machine
Learning
3) Vulnerabilities
4) Policies
5) Risks
Machine learning – Azure AD uses ML to detect risk or anomalies or suspicious incidents which could
indicate potentially compromised identities.
Using this data. Identity
protection generates reports and alerts, enabling you to evaluate the detected
issues and take appropriate mitigation or remediation actions.
This data also
used when evaluating conditional access policies to determine automatic remediation
of user or sign-in risks.
Vulnerabilities – are weakness
in an environment that can be exploited by an attacker.
Azure AD identity Protection identifies these vulnerabilities and presents then in the Overview Dashboard. Clicking on each one provides more information and recommendations on how to re-mediate them, strengthening the security score of the organization.
Policies – in order to take
advantage of risks and vulnerabilities detected by Azure AD Identity Protection.
There are three policies we can configure to automate responses to these
potential threats.
1) MFA authentication registration policy –
·
This policy is used to require registration to
the Azure MFA service.
·
The Azure MFA service should be configured beforehand.
·
User communication should occur before implementing
this policy
2) User risk Policy
·
Automatically responds to a user risk (identity
compromise)
·
Policy can be configured to block access to your
resources or require a password change.
3) Sing-in risk policy
·
Used to react to suspicious actions that come
along with the user sign-in
·
Can be configured to block the account or
require MFA
Both policies User risk and sign-in risk work to automate the response to risk detection's in your environment and allow users to self-remediate when risk is detected.
If your organization wants to allow users to self-remediate when risks are detected, users must be registered for both self-service password reset and Azure Multi-Factor Authentication
Microsoft's recommendation is to set the user risk policy threshold to High and the sign-in risk policy to Medium and above.
Notifications – Azure AD ID
Protection send two types of automated notification emails to help admin manage
user risk and risk events.
1) Users
at risk detected email
Emails are sent per incident, risk
levels and recipients are adjustable, email contains Users flagged for risk report.
Once notification received user should immediately be investigated as only one
email would be received
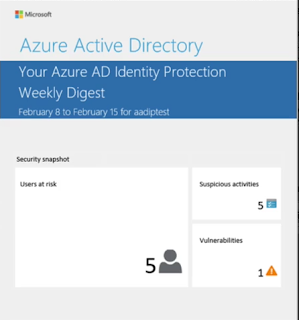
1) Weekly
digest email
Email sent once a week to all
Global administrators, security admins and security readers which contains a
summary of new risk events & includes – User at risk, suspicious activities,
detected vulnerabilities & links to the related reports in identity protection.
Risks –
there are two type of risks Sign-in risk
and user risk –
Sign-in risk means most
likely the authentication request isn’t authorized by the identity owner.
·
Two evaluations of sign-in risk – Real time and aggregate
sing-in risk.
User risk means most likely
the identity is compromised & calculated by –
·
All risky sign-ins
·
All risky events not linked to a sign-in
·
The current user risks
·
Any risk remediation or dismissal actions
Types of risk events: -
·
Atypical travel
·
Anonymous IP addresses
·
Unfamiliar sign-in properties
·
IP addresses linked to malware
·
Leaked credentials
Below are the snippets that you can follow as demo or to configure your Azure AD Identity protection. Steps involved in configurations are -
We are trying on MFA enabled User then this happens and you can opt for verify by MFA to get the access.
·
On-board Azure AD identity Protection.
·
Configure MFA registration policy (optional but recommended)
·
Configure User risk policy.
·
Configure sing-in risk policy.
·
Test the configurations.
To utilize Azure AD ID Protection you should have Azure AD Premium P2 license & you need to on-board this from marketplace as shown below.
Once you select Az AD ID Protection make sure the directory is the one that you want it for and click create. Once you click on Create it would be on boarded and you wouldn't get notification.
Now when you go to A Ad Id Protection you would see all the components that we discussed above and on overview you can find all the events generated due to policy in place under configure.
Now lets configure MFA registration first so that you could utilize this during the user and sign-in risk policy creation. To configure this click on MFA registration >> and fill the information required in the snippet. Select the users that you want to register the MFA and you can also exclude Users.
Under Access its Challenging MFA hence select require Azure MFA registration as shown below
Once access is selected slide enforce policy to ON as shown and its all set for MFA registration. Below snippet also says MFA registration Policy only affects cloud-based Azure MFA. If you have MFA server it will not be affected.
Now its time to configure the User risk-policy just like MFA we need to select the users first and then choose the conditions when this policy would be applicable and finally under controls select the access action either blocked or password change. Below are the highlighted points.
Below snippet is of Conditions and Controls where we select which action in what conditions.
Now finally it looks like this when all the fields are configured and now enforce the policy by sliding it to ON.
Just like MFA and User risk-policy we will also define Sign-risk policy and it would look something like this after selecting all the fields but here we chose require MFA if condition matches.
Now we have defined all the policies and register MFA. In order to perform the demo we can used anonymous try to login with the help of Tor browser and it should detect by Azure AD ID Protection and apply the relevant policy. Its more like if we try to access via Tor browser Azure AD ID Protection would consider this as a threat and if MFA is not enable then it would block the access and MFA is enable already that it would challenge the MFA to grant access. Below are the related snippets.
MFA is not enabled hence access is blocked as shown bwlow
We are trying on MFA enabled User then this happens and you can opt for verify by MFA to get the access.
Since there is some activity and one of the user got blocked and another one challenged for MFA hence few events generated and those would show under Overview. You can see at the begining when we on-boarded this feature it was zero and now we got one.
We are all set and the policy defined to make the maximum use of this feature however we also configure alerts for these scenarios under settings -
Along with alerts we can also configure the weekly digest for Security admins and global admins.
Hope this would informative for you and below link is the source of information






















No comments:
Post a Comment