In the last post we discussed what Azure firewall is and all
the features provided by it and today we are going to perform the demo “deploy
and configure Azure Firewall”.
Azure Firewall controls the outbound network access &
that is an important part of overall network security plan. Azure firewall does
that task or control the traffic by configuring: -
·
Application Rules – define FQDNs that can be
accessed from a subnet.
·
Network Rules – define source address, protocol,
destination port and destination address.
Now to deploy and configure Azure Firewall Demo – lets create
the required Lab
·
Create Resource group
·
Create Virtual Network
·
Create 3 subnets – one for Azure Firewall , One
for Jump server and one for workloads.
·
Create VM in jump and workload subnet
·
Create Firewall
·
Configure Network and application rules
·
Create route
·
Configure route tables
·
Perform the testing
Lets start with creating Vnet in East-us2 as shown in the below configured snippet -
In above snippet you can see , I have created one Vnet and 3 subent in East-us2 location under Arun.RG.
Important thing to notice Azure Firewall needs its separate subnet just like gateway or other NVA's, along with that Subnet name shoould be AzureFirewallSubnet
Now we need to spin two VM's one as Jump server and other one as a workload VM which would help us during the testing of Firewall rule.
Jump server - Windows server with RDP enabled NSG and Public IP needed.
Workload server - Windows server with None RDP and None Public IP.
I am assuming you guys are trained to create VM and Vnet hence skipping those initial steps , all you need to make sure is the setting that i provided for both the servers along with there subnets But we would discuss all the settings of Azure Firewall creation.
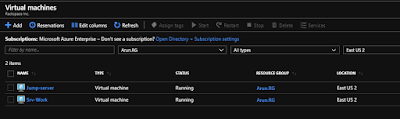
As you can see i have 2 VM's in running state -
Now navigate to Create a resource and search Firewall and click on create as shown below -
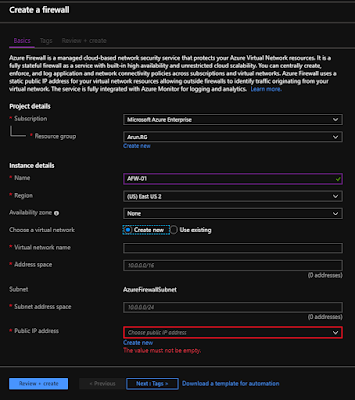
Once you hit the create below window would appear where you need to provide all the information its looking for:-
·
Resource Group
·
Name of the Azure Firewall
·
Region
·
Virtual Network
·
Subnet
·
Public Ip
Now important thing to keep in mind is Subnet name "AzureFirewallSubnet" and public IP that creats is static. Now once you configure all as per the requirement selecting right region and vnet and it would look like this after creation.
You need to copy the private IP as you need that to update the route table.
Now navigate the Route Table and click on Add and it would ask for very basic information as shown in the snippet.
Now once the route table is create you need to click on Route under settings and add a route . Where you provide some name to the route table and -
Address prefix = 0.0.0.0/0 that means all traffic or internet.
Next hop type = select virtual appliance
Next hop address = Private ip of your Azure Firewall
Now you have the route created and we need to associate this route to subnet , here we would associate it with the prod-subnet where all the workloads are lying and whenever they would try to go to internet , they would be re-directed to the firewall.
Now lets go the firewall again and set the Network and Application rule. To configure the rule navigate to Azure firewall and under settings you will find rules and on the right hand side you have Network rule and Application rule.
Lets click on Application rule and click on Add and configure it as shown below -
Priority: 200
Action: Allow
Target FQDN :
Name : Allow-Google
Source Address : 10.0.2.0/24
Protocol:port = Http:80,Https:443
Target FQDNS: www.google.com
Now click on Network Rule collection and click on Add & configure it as shown below -
Priority: 200
Action: Allow
IP Address
Name: Allow-DNS
Protocol: UDP
Source Address: 10.0.2.0/24
Destination Address: 209.244.0.3,209.244.0.4
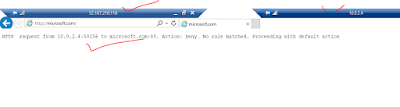
Now both the Rules configured and we are good to test. So to perform testing login to the jump server and RDP workload server and try to browse google.com and microsoft.com. Below snippet confirms the testing.
Google.com works as this is allowed but Microsoft doesn't as its not allowed and even error says the same thing
Reference link -












No comments:
Post a Comment