Managed Identities provides secure method for authenticating Azure resources against other Azure services, without needing to include any credentials.
Managed Identities can be used to authenticate to any service that supports Azure AD authentication without having any credentials in your code.
This feature provides the ability to authenticate on Azure resources "behind the scenes" & does not provide any implicit permissions or authorization , that must still be configured separately.
Lets see some important facts about Managed Identities usage :
Managed Identities can be used to authenticate to any service that supports Azure AD authentication without having any credentials in your code.
This feature provides the ability to authenticate on Azure resources "behind the scenes" & does not provide any implicit permissions or authorization , that must still be configured separately.
Lets see some important facts about Managed Identities usage :
- No need to store credentials in application code.
- Fully managed by MS, so no need to rotate the credentials.
- Automates the creation/registration of an application within Azure AD, Service Principal & Client-ID
- Built-in functionality for Azure resources to securely obtain an authentication token.
- Does not imply any authorization as identity must still be granted permissions.
Managed identities has three main components -
- Principal ID : object id of the service principal
- Client ID : unique identifier generated by Azure AD
- Azure Instance Metadata Service (IMDS) : Rest endpoint accessible to VMs via 169.254.169.254
Types of Managed Identities :
1) System Assigned :
- Fully managed by Azure & directly created for and associated with a resource.
- Exists with the resources & deleted if resource deleted.
- Associate with a single resource
2) User Assigned :
- Created as an individual resource & managed by an administrator.
- Can be associated with one or more Azure services.
Lest Check how to create Managed Identity and provide access permission and finally assign that identity to Azure VM and then try to get an access token using VM assigned idenetity & use it to call Azure Resource Manager.
Navigate to Managed Identity in Azure Portal and create one , follow the snippets :
Lets navigate to Subscriptions and then IAM to provide the Permissions to the Managed identity and in our case we would provide reader access.
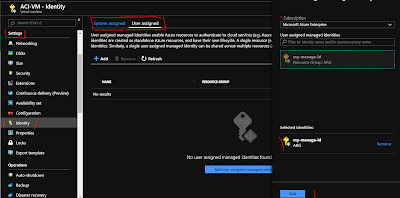
Now lets navigate the Virtual Machine settings and click on identity , here we would add the managed identity as user assigned.
Now as we have discussed above we have completed all the task and assigned managed identity to the VM , Now lets login to the VM and obtain the access token first , via Powershell
$response = Invoke-WebRequest -Uri 'http://169.254.169.254/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https://management.azure.com/' -Method GET -Headers @{Metadata="true"}
Response from above command is in JSON , lets extract it by -
$content = $response.Content | ConvertFrom-Json
$ArmToken = $content.access_token
Finally call ARM using this access token
(Invoke-WebRequest -Uri https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>?api-version=2016-06-01 -Method GET -ContentType "application/json" -Headers @{ Authorization ="Bearer $ArmToken"}).content
You will get a response like this
{"id":"/subscriptions/98f51385-2edc-4b79-bed9-7718de4cb861/resourceGroups/DevTest","name":"DevTest","location":"westus","properties":{"provisioningState":"Succeeded"}}
We will discuss managed Identities with Azure Container Instances in next post.
Refernce link :






thanks !!
ReplyDelete